Listen to the Podcast
6 September 2024 - Podcast #898 - (17:38)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Blood, Sweat, and Tears had a hit with “And When I Die” in 1969. I was 22 years old and thought it was a pretty cool song. Laura Nyro wrote it and sang it on her debut album in 1967. Peter, Paul, and Mary recorded it, too, as did many other artists. More than 50 years later, I’m thinking about it again.
My 77th birthday went whizzing by a few days ago, so I’ve been thinking about the end. Given that both my mother and father died when they were were just 62 years old, although five years apart, I was surprised to hit 70, much less 77. I really didn’t expect to be here now, but I am.
That can’t last forever, though, so what’s next?

Dying seems more complicated than it used to be, in part because of all the services and devices we use to make our lives simpler and easier make it much more difficult for our survivors to gain access to needed resources. How many times have you seen or heard questions from someone who is finding it impossible to gain access to some account or service but can’t because the credentials aren’t available.
And that’s just the beginning. What about bank accounts, credit cards, store accounts, various subscriptions that have been set up with autopay, email accounts, online resources for doctors and other medical care, alarm codes, life insurance policies, loans, cellular and internet plans, and more? I’m encouraged by an online document offered by 1Password that aims to describe a well organized process.
Presumably you already have a will, a living will, and all the other documents that every adult should have and that are even more important during the closing acts, so I won’t be talking about those. See an attorney or, if you cannot afford an attorney, there are some free on-line services that are sufficient for basic needs. Be sure to sign the documents in the presence of a notary and have them notarized.
So you’ve taken care of that. This is about your electronic legacy. Some services, Facebook for example, allow users to name someone who can “memorialize” their account after they die, but I’d rather provide full access to the accounts. That means providing user names and passwords for dozens, or perhaps hundreds, of accounts.
If you have a password manager such as 1Password or LastPass, you can give survivors access to the account by providing the website address, user name, and password in written form. That will allow someone to log in when you’re no longer able to. But watch out if you have enabled two-factor authentication that’s linked to your phone. If your survivors can’t open your phone, they’ll be locked out of the password manager. Most password managers include workarounds that allow accessing the account without using 2FA, but you have to make arrangements while you’re still around. The downside to providing access to a password manager is that survivors may be unfamiliar with how to use the application.
Every password manager I’m aware of includes an option to export all of the information in plain text, and this is probably the most universally accessible option. There is, however, an extreme danger: Password managers encrypt data. If you save a plain text copy on your computer, malware can find it and send it to thieves. If you do this, save the file to a thumb drive and make sure your survivors know where to find it. It’s also wise to print the file and include that with instructions you leave. If you save the file to any device that’s attached to the computer, be sure to delete the file by using a file-destroyer application that overwrites data from the file that would otherwise still be accessible. Deleting a file and emptying the trash simply marks the file as deleted. Until something else overwrites the data, it is still recoverable.
Be sure to repeat the process every six months or so to ensure the data is current.
But what about information that’s not in your password manager? The password that opens the password manager isn’t in the password manager. Most password managers have ways to store secure notes, so the password could be there, but it won’t be much use if your survivors can’t open the password manager because they don’t know the password. Maybe the login password for your computer and the unlock code for your mobile phone or tablet are in the password manager but again the information isn’t useful if your successor can’t open the device. You might want to include this kind of information either in your physical will, in a separate document stored with your will, or in the instructions you provide to open the password manager.
But one of the most important points to remember is that this isn’t a one-time exercise. Come back to it occasionally so you can add new information and update changed information. When you’re dead, it won’t matter to you, but it will matter a lot to your family.
It’s easy to make Microsoft the big bad bully that repeatedly forces users to install unwanted updates, but easy isn’t always right. Some of the updates address security flaws and are intended to keep bad actors out of your computer. Many others improve usability and it’s all too easy to miss these.
Let’s take a look at a few that make my life easier.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
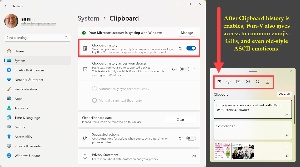 I’ll start with the relatively new Clipboard history feature, which is available in Windows 10 and Windows 11. It’s not enabled by default, so open Settings > System > Clipboard to enable the feature. You can also specify that Clipboard history from one computer is available on another computer. The most useful feature for me is the ability to pin items to the Clipboard so that they are present even after the computer is rebooted. There are some bits of text that I need frequently, and these can be pinned to the clipboard so that I don’t need to type them each time I need them. Example:
I’ll start with the relatively new Clipboard history feature, which is available in Windows 10 and Windows 11. It’s not enabled by default, so open Settings > System > Clipboard to enable the feature. You can also specify that Clipboard history from one computer is available on another computer. The most useful feature for me is the ability to pin items to the Clipboard so that they are present even after the computer is rebooted. There are some bits of text that I need frequently, and these can be pinned to the clipboard so that I don’t need to type them each time I need them. Example:
D:\WEBSITES-Dev\TechByter.com\_development_NO_UPLOAD\TechByter pending
That’s the directory where photographs, screen shots, and other visuals go to be prepared for the website.
Another feature that’s been around for as long as I can remember also involves copy and paste operations. Have you ever copied formatted text from one document or a web page, pasted it into a word processor document, and been annoyed because the text came with unwanted formatting? Then you have to select the text and remove the formatting or modify the pasted text to match the surrounding text. The application may have a menu option that strips the formatting from pasted text, often something like Edit > Paste Special, but it’s faster and easier to just press Ctrl-Shift-V to paste the text without its formatting.
 Although you have to download it separately and it’s not part of the operating system, Microsoft’s remarkable Power Toys utility set is well worth the time needed to obtain it and learn how it works. We’ll return to Power Toys in the next segment.
Although you have to download it separately and it’s not part of the operating system, Microsoft’s remarkable Power Toys utility set is well worth the time needed to obtain it and learn how it works. We’ll return to Power Toys in the next segment.
 Another feature that’s been around since Windows 8 involves pressing the Windows key and X, which provides immediate access to various administrative functions such as computer and disk management, power settings, the Event Viewer, and more. The Windows key opens the Start menu, of course, but it also contains a lot of other magic.
Another feature that’s been around since Windows 8 involves pressing the Windows key and X, which provides immediate access to various administrative functions such as computer and disk management, power settings, the Event Viewer, and more. The Windows key opens the Start menu, of course, but it also contains a lot of other magic.
Examples:
The Control key doesn’t have as much magic as the Windows key, and the functions are all ancient but that doesn’t make them any less useful. These are helpful in word processors and text editors:
Microsoft’s Power Toys utility includes so many features I rely on every day that it’s an essential component on every Windows computer that I’m responsible for. Of the 24 components, I have enabled 20 and use at least half a dozen of them every day. It runs on Windows 11 and any version of Windows 10 from April 2020 and later.
I’ve talked about Power Toys previously, several times, because Microsoft repeatedly adds new features and improves existing features.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
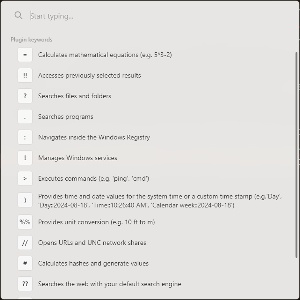 Power Toys Run, for example started out as a quick way to launch applications that you haven’t pinned to the Taskbar or the Start menu. Press Alt-Spacebar to open a text input box, type a bit of the application’s name, select the one you want from the list, and press Enter.
Power Toys Run, for example started out as a quick way to launch applications that you haven’t pinned to the Taskbar or the Start menu. Press Alt-Spacebar to open a text input box, type a bit of the application’s name, select the one you want from the list, and press Enter.
That still works, but now Power Toys Run can perform calculations, search for files and folders, open the Registry editor and navigate instantly to a location, manage Services, execute a command, provide numeric conversions, and switch to the default browser and open a website, go to a network share, search using your search engine, and more. That’s an enormous number of functions in just one of the components.
Not every component has so many options, but spending a bit of time learning how the various features work won’t go amiss.
Do you use CapsLock? That’s one key I have no use for. In the exceedingly rare events when I need to type in ALL CAPITAL LETTERS, I just hold the Shift key. If I ever need a large amount of text in all caps, I’ll type the text normally and then use functions built in to text processors and word processors that convert the case of selected text. It’s easy to activate CapsLock accidentally, so I made a Registry edit several years ago so that pressing the key does nothing. Not everyone is comfortable messing with the Registry, though, and the Power Toys Keyboard Manager allows users to reassign keys. You can disable the key so it has no effect or assign it to some other function.
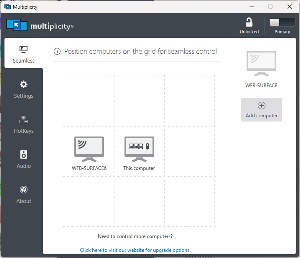 There’s one PowerToys feature I don’t use, but not because it’s not useful. When Mouse Without Borders is running on up to four computers on the same network, a mouse connected to either computer can be used as if it’s attached to any of the other computers. As handy as that is Multiplicity from Stardock Systems is even better because it allows up to nine computers to share a single mouse. I have trouble imagining a use case in which I would need to do that, but it also allows the keyboard that’s attached to the primary computer to be used on the other computers. Multiplicity is part of Stardock’s Object Desktop, which includes Start 11, Fences, Object Dock, Groupy, and other useful Windows utilities. Object Desktop costs about $40 per year and Power Toys is free, so Mouse Without Borders may be adequate if you don’t need to share the keyboard and want to save $40.
There’s one PowerToys feature I don’t use, but not because it’s not useful. When Mouse Without Borders is running on up to four computers on the same network, a mouse connected to either computer can be used as if it’s attached to any of the other computers. As handy as that is Multiplicity from Stardock Systems is even better because it allows up to nine computers to share a single mouse. I have trouble imagining a use case in which I would need to do that, but it also allows the keyboard that’s attached to the primary computer to be used on the other computers. Multiplicity is part of Stardock’s Object Desktop, which includes Start 11, Fences, Object Dock, Groupy, and other useful Windows utilities. Object Desktop costs about $40 per year and Power Toys is free, so Mouse Without Borders may be adequate if you don’t need to share the keyboard and want to save $40.
Find My Mouse is essential. When I’m using Multiplicity, the mouse can be on any of four screens and sometimes it’s hard to find. Pressing the left Control key twice dims either the three screens connected to the primary computer or the tablet’s screen and places a bright highlight around the mouse cursor.
I also don’t use the handy Power Renamer tool, but only because the free Bulk Rename Utility has more features that make it a better fit for my needs.
Environment Variables is a recent addition to Power Toys. The environment is used to store information that the operating system needs, such as the location of driver data, the path that will be searched to locate runnable files, the Windows directory, each user’s temp directory, and more. These settings rarely need to be changed, but those who remember the early days of Microsoft operating systems may recall how easy it was to mess up even something simple like a path modification using the command line.
There’s also an editor for the hosts file, another file that should be touched rarely and a Registry preview utility that gives the user a way to see complex Registry entries before committing them.
The Power Toys utility receives updates every few weeks. In many cases, the updates fix minor bugs and make small improvements to existing components, but occasionally a component receives a much more significant change or an entirely new function is added. If you haven’t yet downloaded Power Toys, now would be a good time to do so. Find more information on Microsoft’s website.
Another in the occasional series of scams perpetrated by idiots.
The SMS text came from an unknown number, so that was strike one. There was no name. No photo. I rarely use LinkedIn and if I had been contacted by someone I wanted to meet, that person would have my email address and I would have their name. Strikes two, three, four, five, and six. Bye bye!
TechByter Worldwide is no longer in production, but TechByter Notes is a series of brief, occasional, unscheduled, technology notes published via Substack. All TechByter Worldwide subscribers have been transferred to TechByter Notes. If you’re new here and you’d like to view the new service or subscribe to it, you can do that here: TechByter Notes.