Listen to the Podcast
17 May 2024 - Podcast #882 - (16:59)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Now and again I think about privacy and security. Probably not as much as I should, but I do think about it. In fact, I know exactly how to make a computer absolutely secure and totally private. I also know that an absolutely secure and totally private computer would be entirely useless.

These are the kinds of things that the US State Department needs to think about. Imagine building an embassy in Moscow, where your building is surrounded by the FSB (Federal Security Service [Федеральная служба безопасности Российской Федерации]), the modern-day equivalent of Vladimir Putin’s KGB (Committee for State Security [Комитет государственной безопасности]). In the old days, the primary concerns were double agents, audio bugs, and service employees such as kitchen and custodial staff, some of whom were required to be citizens of the Soviet Union or, today, Russia.
In 1991, a new US Embassy in Moscow was about half done. It was being built, as required by the USSR, by Russian workers. An inspection of the building revealed hundreds of listening devices that had been built in. And that was before computers had become “a thing”. Much of the work had to be undone and the entire project took 27 years to complete. The “new” US embassy in Moscow opened in 2000 and probably was still not secure.
Sometimes spies attacked simple technology such at typewriters. An article in the IEEE Spectrum magazine describes an event that was the main topic in The Spy in Moscow Station by Eric Haseltine and General Michael V. Hayden in which Soviet bugged IBM selectric typewriters. From the article:
After tens of thousands of fruitless X-rays, a technician noticed a small coil of wire inside the on/off switch of an IBM Selectric typewriter. Gandy believed that this coil was acting as a step-down transformer to supply lower-voltage power to something within the typewriter. Eventually he uncovered a series of modifications that had been concealed so expertly that they had previously defied detection.
A solid aluminum bar, part of the structural support of the typewriter, had been replaced with one that looked identical but was hollow. Inside the cavity was a circuit board and six magnetometers. The magnetometers sensed movements of tiny magnets that had been embedded in the transposers that moved the typing “golf ball" into position for striking a given letter.
Other components of the typewriters, such as springs and screws, had been repurposed to deliver power to the hidden circuits and to act as antennas. Keystroke information was stored and sent in encrypted burst transmissions that hopped across multiple frequencies.
So if somebody really wants to obtain your data and they have the technical expertise, they will. For “technical expertise”, think FBI, CIA, NSA, FSB, JIO, MI5, MI6, Mossad, the 610 office, or any of the hundreds of other security agencies around the globe.
If you want to be positive that your computer is secure: Disconnect the computer from any network (intranet, local area network, and internet); remove any network interface card from the computer; remove any serial ports or internal modem from the computer; remove any parallel port from the computer; remove any USB ports from the computer; disable or remove Wi-Fi or Bluetooth adapters; place the computer inside a windowless room at the center of an RF-shielded building; place security cameras inside and outside the room, making certain that no camera shows what’s on the monitor or what keys the user is pressing; station guards outside the room; allow only one user may be in the room with the computer at any time; log arrival and departure; and prohibit users from taking anything into or out of the room. To avoid break-ins through the roof or tunneling under the floor, the room should be on a middle floor or several floors below ground. Floors, walls, the ceiling, and doors should all be reinforced with quarter-inch stainless steel.
Now your computer is safe and secure. But you’re probably not being sought by the FBI, CIA, NSA, FSB, JIO, MI5, MI6, Mossad, the 610 office, or any of the hundreds of other security agencies around the globe. Less restrictive measures will probably make you safe, but even those measures will make the computer harder to use.
As I said a while ago, I think about this occasionally. A computer protected in this way would be secure, but it would also be unusable. The law of diminishing returns becomes a factor, so the best approach for most of us is to choose a few security tactics that provide substantial returns and forget about the rest. For the computer to be useful, you’ll need it to have access at least to the local network, the internet, disk drives, and printers.
How willing are you to make your computer hard to use so that you and your data will be secure?
Let’s just assume that you have a printer, a network connection, and a Facebook account. You know that your Facebook posts should be shared only with your friends, but is that the setting you use? Yeah, neither do I. Although I try to be careful, I may have occasionally given permissions to a dodgy app.
We have to be careful when it comes to protecting our security and our privacy, but I haven’t been as careful as I should have been. You probably haven’t, either. Privacy should be the default for websites and apps, but that’s not what happens in real life.
The European Union is pushing for more privacy and security. Google might eventually eliminate third-party cookies that track users across the web so advertisers won’t be able to follow users from one site to another.
If something is “free”, you are the product. So long as the web is funded by advertising, you will be the product. Be careful. Beware.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 Password managers do more than just manage passwords. They can help you create good passwords and some have services that let you know if your user name has been involved in a data breach.
Password managers do more than just manage passwords. They can help you create good passwords and some have services that let you know if your user name has been involved in a data breach.
Password reuse is a huge problem. Using the same email and password for more than one account is risky. If you’ve used your Facebook password for a bank account, you may find that your bank account has been emptied. Strong, unique passwords are essential for every significant account, but keeping track of all these passwords manually is impossible. Password managers do this for you.
There are free password managers, but most of the paid services offer useful additional capabilities for a modest fee.
 Backup is the single most effective way to recover from a disaster.
Backup is the single most effective way to recover from a disaster.
If a virus or crook defeats any defense systems you have in place, being able to restore files converts a disaster to an annoyance. Backup isn’t magic. You won’t be back to normal 10 minutes after you discover a problem, but you will be able to recover. “Difficult” is much better than “impossible”.
Several backup methods exist. You can create an image of the entire operating system. You can back up data to cloud-bases services. You can copy essential files to external hard drives or locations such as Google Drive. Consistency is the key.
My online backup constantly copies new and changed files, but there’s also a local backup system that does the same with important active files. I create an image backup of the boot drive twice a week. All data files are also backed up each week to local drives that are attached only during backup. That’s a “belt and suspenders” approach you might find amusing, but I haven’t lost a file in the nearly three decades that I’ve been using this system.
 If a scammer manages to obtain the user name and password you use to log in to your PayPal account, two-factor authentication will safeguard your account. Probably. There are ways around two-factor authentication, but using it makes the account much more secure. Many services now offer this feature, so enable it wherever you can.
If a scammer manages to obtain the user name and password you use to log in to your PayPal account, two-factor authentication will safeguard your account. Probably. There are ways around two-factor authentication, but using it makes the account much more secure. Many services now offer this feature, so enable it wherever you can.
Two-factor authentication requires you to confirm your account with more than just a user name and password (“something you know”) by adding a third component (“something you have”). So a scammer might have both parts of the “something you know” component, but it’s much harder to gain access to the authentication code. 2FA means you may spend another five seconds logging in, but 2FA alone massively improves security. Some password managers can also perform the authenticator function, so the extra time required is close to zero.
Understanding that perfect security is unworkable, implement security measures that address the most common severe threats. Making your computer secure may seem to get in the way, but security procedures don’t need to make the computer harder to use and they do protect your data, your money, and your identity from thieves.
Your Windows computer has at least one disk drive that’s formatted as NTFS, but some devices that will be used with the computer should use another format.
The NT in NTFS stands for New Technology, which is was in 1993 when it was first used with Windows NT 3.1. The FS stands for File System. NTFS was designed for larger disk drives and supports functions needed by modern operating systems.
When somebody builds a drive large enough to hold 16 exabytes of data, NTFS will handle it. What’s more, individual files can be up to one exabyte. An exabyte is one million terabytes, so that would be one gigantic file and a drive that can hold 16 million exabytes is all but unthinkable today. An earlier disk format, FAT32 (File Allocation Table) couldn’t deal with files larger than 4 gigabytes and the maximum disk partition size in just two terabytes.
NTFS also handles journaling that tracks changes that haven’t yet been written to the drive. This largely eliminates data loss if the drive unexpectedly loses power. Permissions similar to those used by Unix and Linux are supported by NTFS drives and so is encryption. VSS (Volume Shadow Copy Service) is an NTFS feature used by backup programs to back up files that are in use when the backup is running. Without VSS, files that are in use could not be backed up.
Seems ideal, doesn’t it. Why would you want to use another file system? Well, NTFS doesn’t work with MacOS computers, some older Linux systems, and Android devices. So if you have thumb drives, external hard drives, or solid-state drives that need to be connected to non-Windows devices, you should use another format.
You could still use the MS-DOS FAT system that persisted through Windows 3.1. That would be a bad choice today. Either FAT32 or exFAT (Extendsible FAT) are acceptable choices and exFAT is the better option because it supports the same drive and file sizes NTFS does, and it’s compatible with MacOS computers, Linux systems, and Android devices.
If you’re sure a new device will never be connected to any other computer, choose NTFS because of its clear advantages. Otherwise, think about choosing FAT32 or exFAT.
When you open YouTube, you’ll see a screen full of icons. Video producers often create title images instead of using a frame from their video. Sometimes these are helpful, but it seems that many are simply ClickBait intended drag you in.
Here’s some good news: There’s a quick, easy way to get rid of ClickBait. The ClickBait Remover for YouTube is available for Chrome-based browsers and for Firefox. As frequently happens, there seems not to be an option for Safari users.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
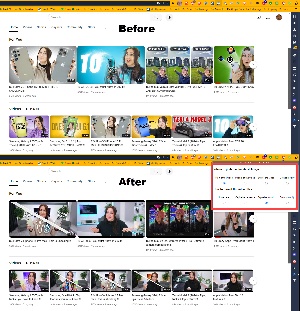 It’s a free, lightweight extension that allows the user to decide whether to replace thumbnails provided by the video creator with the first or last frame from the video, replace it with a random frame from the middle or the video, or to leave it alone. It can also control whether the title appears as the video producer created it (often all caps), all lower case, or title case.
It’s a free, lightweight extension that allows the user to decide whether to replace thumbnails provided by the video creator with the first or last frame from the video, replace it with a random frame from the middle or the video, or to leave it alone. It can also control whether the title appears as the video producer created it (often all caps), all lower case, or title case.
ClickBait Remover for YouTube works everywhere on YouTube including the homepage, trending page, subscription page, and channel pages.
If you dislike clickbait thumbnails, this is one way to get rid of them, but it would be helpful to add an option that would allow the user to explicitly allow thumbnails on those channels that use them responsibly. That would substantially increase the plug-in’s complexity and it is, after all, offered for free.
One workaround for users who want to see thumbnails for channels that they’re subscribed to would be to turn to extension off when they visit one of those channels.
To obtain ClickBait Remover for YouTube in Firefox, visit the add-ons page. For all Chrome-based browsers, use either the browser’s extension finder or the Chrome Web Store.
TechByter Worldwide is no longer in production, but TechByter Notes is a series of brief, occasional, unscheduled, technology notes published via Substack. All TechByter Worldwide subscribers have been transferred to TechByter Notes. If you’re new here and you’d like to view the new service or subscribe to it, you can do that here: TechByter Notes.