Listen to the Podcast
22 Mar 2024 - Podcast #874 - (18:44)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
The most common method scammers use to take your credit card or bank account for a trip to a dark alley isn’t a credit card skimmer. It’s not eavesdropping on an unencrypted Wi-Fi connection. The easiest method to obtain a user’s login ID and password is simply to ask for them.
Two-factor authentication tilts the playing field a bit in our favor, but crooks have found a way around those safeguards and not every organization yet supports two-factor authentication. Certainly you would refuse to give someone your login credentials if you received a call from someone you don’t know and the caller said, “Look, you don’t know me, but would you please give me your user name and password for your bank so I can empty your bank account?”
But they don’t ask that way.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
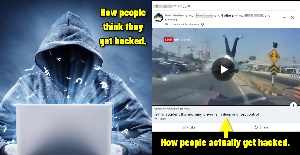 One common method that has seen a lot of use this year involves phony messages on Facebook that appear in your feed because you or someone you know is tagged. The message laments someone’s death, but never names the person. In some cases, the unnamed person has died of natural causes, but more often it’s the result of a wreck, complete with a shocking image from a news story or a dash cam. What appears to be a link to a YouTube video or a video on another legitimate source is shown, but the link is not to the named source.
One common method that has seen a lot of use this year involves phony messages on Facebook that appear in your feed because you or someone you know is tagged. The message laments someone’s death, but never names the person. In some cases, the unnamed person has died of natural causes, but more often it’s the result of a wreck, complete with a shocking image from a news story or a dash cam. What appears to be a link to a YouTube video or a video on another legitimate source is shown, but the link is not to the named source.
The link could be to a site that loads malware onto your computer, or it might want you to log in to a social media account, which allows the scammer to steal the user name and password. This is effective because far too many people use the same credentials for social media accounts and banks.
Or you receive an email that pretends to be from your bank, explaining that your money is at risk from an embezzler who works at the bank, and offering to safeguard your money by helping you to move it to a secret location where the embezzler can’t get it. That trick makes the process easy because the scammer never needs to obtain your credentials; instead, they’ll convince you to do all the heavy lifting, move your money to where they can get it, and then disappear without a trace.
More traditional techniques involve sending an email purporting to be from your bank. The message may say that the bank has noticed what appears to be a fraudulent attempt to use your credit card. You’ll need to click a link in the message to confirm your identity so that they bank can halt the transaction. The link will take you to a page that looks like your bank’s login page, but it’s really on a server the scammer is running. When you enter your user name and password, the crook gets them and passes them on to the bank. You’ll be logged in to your account, but the crook will be tagging along. You’ll think that you’ve logged out later, but the crook stays behind, changes your password and the phone number used for two-factor authentication, and then transfers your money to their account.
The message may have an attachment that’s supposed to show details of a purchase that’s been charged to your account. The attachment installs malware on your computer so that the crook has full control of it.
Crooks also use SMS messages claiming to be from legitimate organizations. And they can plant malware on websites and then use an honest website to display an alarming message on computers used by website visitors. The SMS message or pop-up alert can warn that your computer is infected and say that you must contact tech support immediately for assistance. A phone number is provided and the scammers will try to talk anyone who calls into paying for protective software that’s useless or worse. If the user refuses the offer, the scammer will try to gain access to the user’s computer by promising to fix the problem at no charge. The “technician” will install malware on the computer.
These are just a few of the techniques thieves use to convince people to hand over their valuable information. Scammers are clever enough to always be on the lookout for new approaches. The messages may claim to be an alert that your account has been accessed by someone in a foreign country, that there’s a suspicious transaction on your bank account or credit card, that the IRS or Social Security needs a response from you, that an expensive computer has shipped to you, that you have signed up for or cancelled a service, that a package could not be delivered, or any of hundreds of topics scammers have found to be effective.
STOP! WAIT! Read the message again. Several times. Look for clues that it’s a fraud. Crooks want you to act without thinking and include notes of emergency in their messages. Microsoft, the FBI, the IRS, and most other organizations will not contact you by email. Those that do may occasionally include a clickable link, but you should never use it. If you receive a message from your bank, don’t click the link. Instead, log on to the bank’s website using your normal method or call the bank. If you call, use the phone number on the bank’s website, not a number that’s included in the suspect message. Remember that a bank will never ask for your user name or password by phone. If the bank calls you, they will be able to tell you the full account number so that you can validate them, not the other way around.
PhishTank is a useful organization where users can submit, verify, track,and share phishing data. There’s a database of confirmed phishing URLs for sites that attempt to steal user information by making users believe they are accessing a legitimate service. Users submit suspected phishing URLs and other users then can vote to verify the status as a phishing site or dispute if. When a URL receives enough valid votes, it is declared a confirmed phishing site.
Remember that no matter what protective software is running on your computer, you are the final line of defense.
Everything you share on the internet makes it easier for scammers to convince you that you know them. Use protective software such as antivirus and antimalware applications. Enable a VPN when shopping or accessing financial site, particularly when you’re not at home on your own private network. Enable two-factor authentication on every website that offers it.
And be a bit paranoid. You are the final line of defense. You are the one who can recognize a threat and shut it down. You are the one who can avoid clicking on a dangerous link. Don’t be the phish who gets caught in a crook’s net.
The best way to deal with a cloned or hijacked Facebook account is to avoid having the account cloned or hijacked in the first place. The best preventive measures start by learning what might attract scammers.
In this week’s main article, I described some of the dangers to watch for, ways to eliminate trouble by not clicking links, not falling for obvious scams, and not cheerfully handing over your credentials to crooks. There’s a quick and easy way to see your Facebook page as a thief might see it.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
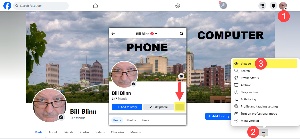 Start by logging into your account on a computer or a mobile device. On a computer, go to your account page, click the ellipses dots at the right side of the menu and choose View As. The process is similar on a phone. Navigate to your Timeline page and click the three ellipses dots. Then choose View As from the next menu. This will display your page the way others, including crooks, will see it.
Start by logging into your account on a computer or a mobile device. On a computer, go to your account page, click the ellipses dots at the right side of the menu and choose View As. The process is similar on a phone. Navigate to your Timeline page and click the three ellipses dots. Then choose View As from the next menu. This will display your page the way others, including crooks, will see it.
Take a look at each section on the About tab. The less information visible here, the less attractive your account will be to scammers. When you move on to the Friends tab, the safest setting will report “No friends to show” as I described earlier. The Photos and Videos tabs will display any items you’ve shared publicly. Likewise check-ins that you posted publicly. The most important setting for me is to hide all friends from everyone but me. If scammers can’t see your friends, they’ll have little interest in cloning your account.
If you find information or images that you don’t want the public to see, visit Facebook’s Privacy Settings section and modify the settings to make the information disappear. And at the risk of repeating myself one time too many, it’s best to set your friends list so that only you can see them.
I recently found a Facebook group that can help frustrated Facebook users. To the best of my knowledge Facebook has no users other than frustrated ones. Platform Help, which used to be called Facebook Help, is a private group where you can find ways to fix a lot of annoyances. Keep in mind, though, that the group may be operated by people who can help with Facebook annoyances but it is not operated or supported by Facebook. That, of course, would be too much like offering a needed service. Because Platform Help is a private group, you’ll need to request admittance.
 If you deal with Facebook on a mobile device, you’re mainly stuck with the Facebook app, but both Social Fixer and Fluff-Busting Purity can eliminate some of the worst annoyances if you view Facebook on a computer. Anyone who interacts with Facebook on a Windows, MacOS, or Linux computer, is probably spending more time being annoyed than they should. Check out either FB Purity or Social Fixer. My preference is Social Fixer, but they’re both good applications. Pick one or the other, though; if you have both enabled, the results are unpredictable.
If you deal with Facebook on a mobile device, you’re mainly stuck with the Facebook app, but both Social Fixer and Fluff-Busting Purity can eliminate some of the worst annoyances if you view Facebook on a computer. Anyone who interacts with Facebook on a Windows, MacOS, or Linux computer, is probably spending more time being annoyed than they should. Check out either FB Purity or Social Fixer. My preference is Social Fixer, but they’re both good applications. Pick one or the other, though; if you have both enabled, the results are unpredictable.
Facebook will always be an annoyance, but it is possible to tame some of the worst annoyances.
If your default web browser is Microsoft Edge or if your default is some other browser, but you don’t mind it when Microsoft forces you to use Edge, skip this section. But if you don’t want Edge to take over without asking, here’s a solution.
The easiest solution, if you detest Edge, is simply to remove it from the computer. But there’s a problem. There is no way to “simply” remove Edge. As is typical of Microsoft, the company makes the process more difficult than it should be. Removing Edge was deceptively simple, but when Windows noticed that it was gone, it reinstalled the browser. Later versions of Windows makes uninstalling Edge impossible in the United States.
This doesn’t happen in European Union countries because Microsoft needs to comply with the EU’s Digital Market Act. Europeans can also disable the search bar, which is powered by Microsoft’s Bing search engine. They can also remove Microsoft’s Photos, Camera, and Cortana apps. Microsoft should make these options available worldwide, including in the United States, but don’t hold your breath.
 If your version of Windows is version 23H2 or earlier, it is possible to remove Edge and keep it from returning, and Tom’s Guide describes the process in detail. That’s not the solution for me, though. I like having Edge on the computer because it’s not a bad browser. I simply want Edge to run only when I explicitly run it.
If your version of Windows is version 23H2 or earlier, it is possible to remove Edge and keep it from returning, and Tom’s Guide describes the process in detail. That’s not the solution for me, though. I like having Edge on the computer because it’s not a bad browser. I simply want Edge to run only when I explicitly run it.
If you don’t mind having Edge on your computer, you may still resent Microsoft’s heavy hand that forces you to use it when you click a link in a Microsoft App. If you’re using Word, Outlook, or Excel and click an embedded link, Edge answers even if you have specified some other browser as the default. It’s not a big deal to close Edge after visiting the site, but it’s infuriating for this to be needed. Well, maybe not infuriating. But it is annoying and I don’t like to be annoyed by a computer.
I could switch to Libre Office and avoid the problem, but Libre Office doesn’t include some of the important components that are included with Microsoft 365: OneNote, for example. Moving to Europe would be another solution, but I don’t speak any of the languages, except for a smattering of Russian—and I’m certainly not going to move to Putin’s Paradise. What about English? Well, Great Britain is no longer in the European Union.
So the solution turns out to be easy and free. Visit GitHub and download MS Edge Redirect. At the time I wrote this, the stable version was 0.7.5.3 and the beta version is also available from GitHub as well as from Winget, Scoop, and Chocolatey. It runs on any version of Windows 8.1 and later.
 MS Edge Redirect switches all links that attempt to open in Edge to your preferred browser and it also stops search requests from opening in Bing. Instead, you can set your own preferred search engine.
MS Edge Redirect switches all links that attempt to open in Edge to your preferred browser and it also stops search requests from opening in Bing. Instead, you can set your own preferred search engine.
 The installation is a bit puzzling. Three modes are shown, one is selected by default and the third is recommended. The Europe mode should not be used in the United States because it will tamper with the computer’s locale settings. US users have the option of Service Mode (selected by default) and Active Mode (recommended). On the first go, I used Service Mode but found that the installation didn’t work as expected. On the second try, I switched to the recommended Active Mode.
The installation is a bit puzzling. Three modes are shown, one is selected by default and the third is recommended. The Europe mode should not be used in the United States because it will tamper with the computer’s locale settings. US users have the option of Service Mode (selected by default) and Active Mode (recommended). On the first go, I used Service Mode but found that the installation didn’t work as expected. On the second try, I switched to the recommended Active Mode.
The installer selected Edge Stable, which is the version installed on my computer and I also switched Bing Discover to Google, Bing search to DuckDuckGo, MSN News to DuckDuckGo, MSN Weather to AccuWeather, Bing images to DuckDuckGo, and the PDF viewer to my system’s default viewer.
So now Edge is still installed, but it opens only when I want it to, at least most of the time. I have found some instances in which MS Edge Redirect doesn’t work. Microsoft Loop, for example, which is intended to perform some of the tasks I use OneNote for, still manages to call Edge instead of my preferred browser. This gives me yet another reason not to use Loop.
TechByter Worldwide is no longer in production, but TechByter Notes is a series of brief, occasional, unscheduled, technology notes published via Substack. All TechByter Worldwide subscribers have been transferred to TechByter Notes. If you’re new here and you’d like to view the new service or subscribe to it, you can do that here: TechByter Notes.