Listen to the Podcast
20 January 2023 - Podcast #815 - (16:41)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
It wasn't published then because of a back injury, spinal surgery, and physical therapy that kept me away from the office and studio. This is the third of three delayed programs.
Some people refuse to use two-factor authentication because it takes more time and effort to connect with a website, but avoiding two-factor authentication (2FA) is a bad way to save time. So maybe 2FA isn't the new normal just yet, but it should be.
I've been thinking about this since I read an article by Jack Wallen on TechRepublic. The premise is that 2FA is failing. Although that may well be true, don't let it keep you from using a password manager, 2FA, and any other security options the website offers.
The more important a site is, the more important it is to have sufficient security measures in place to protect it. By "important", I don't necessarily mean Facebook, although the person who gains access to you Facebook account can do a lot of damage. What I mean is financial websites — your bank, insurance portal, PayPal, and such. Wallen says that his PayPal account was hacked recently and it wasn't the first time it had happened, or the second. Wallen discovered the problem and acted quickly, but still — if it happened to a guy who knows his way around security, it could happen to you.
I've been lucky so far. A Visa card number was stolen a long time ago and a crook obtained my American Express card information about two years ago. I noticed the attempted charges, reported them, and the cards were promptly replaced.
Like Wallen, I use a password manager. For important accounts, I use complex passwords such as X_@q{?f2r^saYbZyD}. That is not one of my actual passwords, but many of them are 18 characters long or longer and contain upper and lower case letters, numbers, and symbols. I also enable 2FA on every account that permits it.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
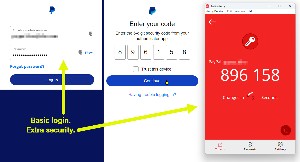 When I log in to my PayPal account, LastPass provides the user name and password, but then PayPal asks me for a six-digit number that changes every thirty seconds. I can obtain this number from an authenticator application such as Authy or the Google Authenticator. This number is delivered to me securely via the authenticator and not via an SMS message. The authenticator is a standalone application on the phone, computer, or tablet — not via the browser.
When I log in to my PayPal account, LastPass provides the user name and password, but then PayPal asks me for a six-digit number that changes every thirty seconds. I can obtain this number from an authenticator application such as Authy or the Google Authenticator. This number is delivered to me securely via the authenticator and not via an SMS message. The authenticator is a standalone application on the phone, computer, or tablet — not via the browser.
 PayPal includes several security options. Among the most important are the ability to change the password, enable or disable 2FA, and check which devices have successfully logged in.
PayPal includes several security options. Among the most important are the ability to change the password, enable or disable 2FA, and check which devices have successfully logged in.
I consider it unimportant to change passwords frequently. Unless you have reason to believe that a password has been compromised, just leave it alone. Some of my passwords have been in use for a decade or more. Using 2FA with an authenticator app is much more important. It's also good to occasionally check which devices have accessed your account recently. If you see one that you don't recognize, block it, and this would be a good time to change the password.
The fault Wallen sees with the 2FA process doesn't involve password managers, long and complex passwords, or authenticator apps; instead it's with 2FA procedures that use SMS messaging to deliver the six-digit code. As Wallen put it, "When those 2FA codes are submitted via SMS text, they can be intercepted by the wrong people." If those people already have your user name and password, they can quickly log in as you, change the password, and start using your money.
 If you're still using simple passwords, reusing passwords, not using a password manager, or not taking advantage 2FA whenever possible, it's time to get up to date. The thieves aren't stupid and sooner or later somebody will find a way to obtain your user name (which is probably your email address) and your password. Without the security of 2FA, your account and your money are in jeopardy.
If you're still using simple passwords, reusing passwords, not using a password manager, or not taking advantage 2FA whenever possible, it's time to get up to date. The thieves aren't stupid and sooner or later somebody will find a way to obtain your user name (which is probably your email address) and your password. Without the security of 2FA, your account and your money are in jeopardy.
It's long past time for 2FA to be the standard for every account. It's also time for those organizations that use SMS messaging for 2FA to up their game and switch to using an authenticator. Authenticator apps are probably at least one order of magnitude more difficult to defeat.
It's true that all security measures make your life slightly more complicated, but if taking an extra ten seconds to acquire and submit a six-digit code from an authenticator to connect to your bank eliminates the pain of having to report stolen credentials, obtain a new credit or debit card, or even deal with identity theft, that seems like an exceptionally good trade-off to me.
NOTE (2023-01-19): One of the illustrations in this article shows LastPass. Because of security concerns, I stopped using LastPass in January and I'm evaluating replacements. I'll have a full report on 10 February 2023.
Recently I wrote about the "oh-no second", the time that elapses after you've done something stupid until you realize you've done something stupid. That's the starting point for today's story about finding a small hole in my backup system.
Before getting to the hole in the backup plan, I have to provide some backstory because that's where the real stupidity occurred. The hole that it exposed was simply an oversight that had an easy solution.
So — the stupidity.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
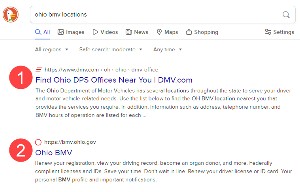 I needed to visit an Ohio Deputy Registrar and wanted to check the hours of operation and the requirements for that task I needed to complete. A search for "ohio bmv locations" returned a lot of results and I clicked the one at the top of the list without noticing that it would not take me to an ohio.gov site. (1) is the link I clicked and (2) is the legitimate link.
I needed to visit an Ohio Deputy Registrar and wanted to check the hours of operation and the requirements for that task I needed to complete. A search for "ohio bmv locations" returned a lot of results and I clicked the one at the top of the list without noticing that it would not take me to an ohio.gov site. (1) is the link I clicked and (2) is the legitimate link.
Instead, I was taken to dmv.com. I plead inattention to details as my only defense.
 A graphic on the page showed me that I was at DMV (in large letters) .com (in much smaller letters) and said a non-government site in minuscule letters. That's probably enough to keep the site just barely legal.
A graphic on the page showed me that I was at DMV (in large letters) .com (in much smaller letters) and said a non-government site in minuscule letters. That's probably enough to keep the site just barely legal.
Nothing bad would have happened if I had followed my normal procedure when the site displayed a message saying www.dmv.com wants to show notifications. I always (always, always, always) click BLOCK.
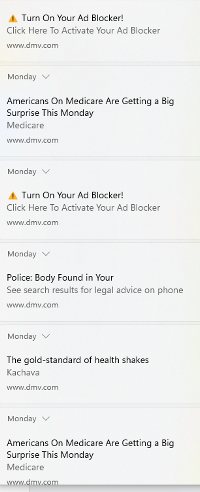 This time I didn't. And instantly notifications started appearing. Often three or four at a time, all of them with scammy offers. Once again I plead inattention to details as my only defense.
This time I didn't. And instantly notifications started appearing. Often three or four at a time, all of them with scammy offers. Once again I plead inattention to details as my only defense.
The alerts even included two scams labeled Turn On Your Ad Blocker! Perhaps you already suspect that I clicked exactly none of these offers.
Although I knew that nothing had been installed on the computer, I looked at uninstall options and found exactly what I expected: Nothing. There were no unexpected processes running on the computer and there were no new entries in either the Start Menu's Startup folder or in the Registry. The problem was limited to the browser.
That's good because it meant the fix would be relatively easy, but bad because it meant that deep-cleaning the browser would eliminate information that I would then have to re-enter or re-collect by visiting the website. This isn't a big deal, but it is an annoyance.
Also, for the past few months, I've been playing Chrono Quest each morning and cleaning the browser would eliminate information about my wins, game time average, and winning streak. That was just sufficiently annoying that I wanted to find a way to fix it. The fact that it was a slow day helped in this regard.
So I blew away Vivaldi's cache, internet history, cookies, session files, download information, temp files, and metrics, and then compacted the Vivaldi database. When I opened the browser again, the dmv.com annoyances were gone. But so were files and data associated with other websites.
I wanted that information back and I've bragged about my backup system, but this is where I found the hole. And that's coming up next, along with the solution.
Continuing the story: Getting rid of the dmv.com annoyances took less than 15 minutes, but it left the browser with none of the information I wanted it to have. The bookmarks were still there, of course, along with the extensions I use, but sites that I visit frequently no longer recognized me.
"Easy," you're probably thinking "He has lots of backups. No problem!" Well, yes and no. I had the files, but they wouldn't be easy to restore.
The data for the browser is stored on drive C and that's the one drive I don't do a file system backup of. Instead, I make an image backup every Wednesday and every Sunday using two different disk drives to ensure that I have the operating system fully backed up.
Drive C also doesn't get backed by the cloud-based backup system because CrashPlan is not designed to back up system and application files. It also isn't designed to download the operating system or applications even if I had managed to back them up to the cloud. I could back up data files from the C drive, but I don't because the few data files on drive C are already backed up to Microsoft's One Drive.
The files I wanted were in %localappdata%, which is a shortcut for C:\Users\{USERNAME}\AppData\Local\. The files I needed to restore are further down the directory tree in Local\Vivaldi\User Data\Default\. Although I believed that restoring files from backup would cause no problems, I renamed the Default directory to Default-OLD and created a new Default directory.
To get the files back, I needed to first restore the Sunday disk image to a partition on another disk. Fortunately I had such a disk lying around. It had previously been used for music files that I took with me to the office. But I haven't gone to an office for five years and I had formatted the drive and named it "Spare Disk" so that I could use it if a need arose, as it had just done.
The process of restoring the Windows partition image took more than four hours, but didn't require my attention. It simply ran in the background while I was working on other things. The most recent image backup was from Sunday and the day of stupidity was the following Tuesday, so I knew that I would lose two days worth of history from Chrono Quest. That's still better than losing all of the history.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 After the restore process completed, I had a Windows partition on drive L that replicated the partition on drive C, but was two days old. I drilled down to Users\willi\AppData\Local\Vivaldi\User Data\Default on both drives and then copied the files from drive L to drive C.
After the restore process completed, I had a Windows partition on drive L that replicated the partition on drive C, but was two days old. I drilled down to Users\willi\AppData\Local\Vivaldi\User Data\Default on both drives and then copied the files from drive L to drive C.
When I started the browser, all of the sites that I visit frequently recognized me. And — what I really wanted — Chrono Quest had my historical data up to the previous Sunday, just two days ago.
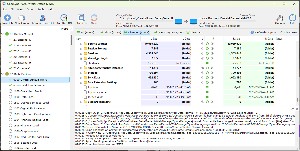 To fix this particular hole, in case I ever again accept notifications from a rogue site, I set up two automatic GoodSync processes that copy the contents of Vivaldi's Default folder to my local backup drive every day at 7am. One of the jobs runs Monday, Wednesday, Friday, and Sunday and the other runs on Tuesday, Thursday, and Saturday. That's enough to provide time to recognize a problem and correct it before bad files overwrite good files. If I don't notice the problem, I still have two weeks to find it and use the option to restore from the image of drive C.
To fix this particular hole, in case I ever again accept notifications from a rogue site, I set up two automatic GoodSync processes that copy the contents of Vivaldi's Default folder to my local backup drive every day at 7am. One of the jobs runs Monday, Wednesday, Friday, and Sunday and the other runs on Tuesday, Thursday, and Saturday. That's enough to provide time to recognize a problem and correct it before bad files overwrite good files. If I don't notice the problem, I still have two weeks to find it and use the option to restore from the image of drive C.
The first rule to remember here is Don't do something stupid, but that important rule has an even more important corollary: When you do something stupid, have a way to fix it.