Listen to the Podcast
6 January 2023 - Podcast #813 - (16:51)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
It wasn't published then because of a back injury, spinal surgery, and physical therapy that kept me away from the office and studio. This is the first of three delayed programs.
The latest desktop computers are less often big boxes that make a lot of noise and take up much of the desk. Increasingly, they are notebook computers with an external mouse, keyboard, and screen. Making the right choice depends on knowing how you want to use the computer.
It's hard to pin down accurate numbers, but research firms that specialize in computer data generally agree that mobile computers are taking the lead. One problem is that some people have been able to replace all of their computing devices with a phone. The most-used operating system is Android, but can you replace a desktop, notebook, or tablet with a phone? I couldn't, even though keyboards, mice, and monitors can be connected to some phones.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 Video editing is one activity that calls for desktop power. >>>
Video editing is one activity that calls for desktop power. >>>
Statcounter says mobile devices have 51% of the market, compared to 46% for desktop systems 3% for tablets. But Statcounter gets its figures from websites. Devices that don't connect to websites monitored by the service don't count. And those figures are for North America. Worldwide, the figures are 60%, 39%, and 2% respectively. In Europe, it's 52%, 46%, and 3%.
Apple sells a lot of notebook computers, but three Windows PC manufacturers account for 60% of the laptop computers sold — Lenovo, Dell, and HP. According to WebTribunal, Lenovo has a 24% share of the PC market. By comparison, Apple has a bit less than 7% of the market. Lenovo is a Chinese company. Although Dell, HP, and Apple are not Chinese companies, most of their computers are manufactured in China.
I used to joke about the perfect lens for a 35mm film camera. I wanted a zoom lens that would cover the range from 10mm to 1000mm with constant f/stops across the range, and no pincushion or barrel distortion at any length. The lens would be no more than six inches long, weigh less than two pounds, and cost $250. Needless to say, no manufacturer ever created such a lens because, in part, it would violate several laws of physics. Likewise, there is no single perfect all-purpose computer.
Notebook computers are portable and come with built-in Wi-Fi capabilities. When you buy a new notebook computer, it's essentially ready for use as soon as you take it out of the box. Most notebook screens have exceedingly high resolution, and the computers use much less power than a desktop computer.
That last point isn't very important if you have just one or two computers in the house, but an enterprise that replaces hundreds or thousands of power-hungry desktop systems with notebook computers can expect to see their usage of electricity decline.
 But keyboards on notebook computers are often hard to use and you won't find an articulated keyboard on a notebook computer. Because the screen has high resolution, text will be small and difficult to read. Notebook computers cost considerably more than technically equivalent desktop systems and they're more difficult to upgrade if you need more memory or disk space.
But keyboards on notebook computers are often hard to use and you won't find an articulated keyboard on a notebook computer. Because the screen has high resolution, text will be small and difficult to read. Notebook computers cost considerably more than technically equivalent desktop systems and they're more difficult to upgrade if you need more memory or disk space.
Because notebook computers are portable, they're more likely to be lost, damaged, or stolen.
 Desktop systems can use CPUs that wouldn't work in a notebook computer because it would be too large or too hot for a notebook's small case. Desktop systems have components that can be easily removed so upgrades are relatively easy, and there's often space in the case for additional disk drives. Because they aren't portable, desktop systems are less likely to be stolen.
Desktop systems can use CPUs that wouldn't work in a notebook computer because it would be too large or too hot for a notebook's small case. Desktop systems have components that can be easily removed so upgrades are relatively easy, and there's often space in the case for additional disk drives. Because they aren't portable, desktop systems are less likely to be stolen.
If performance is the absolute top priority, a desktop computer is definitely the right choice. I've been using a notebook computer on the desktop for nearly a decade, but if most of my day was consumed by video production, I would probably still want a desktop system.
 Except for that, my preference is for a notebook computer with external monitors, a mouse, and a keyboard. Add a dock, USB ports, and a disk enclosure for four external disk drives and the result is all of the storage and user interfaces that I'd have with a desktop system, although at a somewhat higher price and a bit lower overall performance.
Except for that, my preference is for a notebook computer with external monitors, a mouse, and a keyboard. Add a dock, USB ports, and a disk enclosure for four external disk drives and the result is all of the storage and user interfaces that I'd have with a desktop system, although at a somewhat higher price and a bit lower overall performance.
I can't make a valid case for portability because the four external drives need to be present. They are the devices that hold all of the data. It's true that I could create two separate login procedures, one of which would eliminate the need for the external drives, but I can use a Windows Surface 6 Pro tablet, an IPad, or even the smart phone for those rare times when I must have a mobile computing device.
Another big advantage for me is that the notebook computer takes up little space and I'm able to place both a MacBook Pro and the Windows notebook on the desktop and share the keyboard, mouse, and screens between them.
So the next time you're looking for a new computer, don't rule out either desktop or notebook systems. Analyze what's important to you and then made a decision based on your requirements.
Around the end of August, LastPass users received a message with the subject "Notice of Recent Security Incident." That's scary, of course, and the subject line doubtless caused a lot of people to open the message, expecting the worst.
NOTE: After this report was written, LastPass suffered another breach, one that seems to be a lot more serious. I'll have a follow-up in an upcoming report.
It wasn't that bad. The message said that their internal security processes "recently detected some unusual activity within portions of the LastPass development environment." The response was exactly right: "We immediately initiated an investigation, deployed containment and mitigation measures, and engaged a leading cybersecurity and forensics firm." The message didn't identify the forensics firm, but that's probably a contractual thing. The company says they contained the threat, implemented additional enhanced security measures, and see no further evidence of unauthorized activity.
They also explained how "an unauthorized party gained access to portions of the LastPass development environment." A single developer account had been compromised and the intruder "took portions of source code and some proprietary LastPass technical information." As serious as that may sound, it's not troubling.
Anybody can obtain the source code for KeePass, KeePassX, Bitwarden, and several others. Bitwarden is a commercial enterprise, like LastPass, but Bitwarden is an open-source project while LastPass is proprietary. So the fact that some bad player managed to get into the development system isn't a particularly large concern. The fact that LastPass noticed the activity promptly and shut it down is good. Even better is the fact that they then went public with the announcement.
To understand why gaining access to the source code isn't a big deal, it's also important to know that large software companies typically have three systems that are not directly connected to each other: Development, staging, and production.
Those of us who use LastPass communicate with the production system. This is where our encrypted passwords reside. Nobody at the company can see your data because it's encrypted and because the master password isn't stored with your data. That's why users are cautioned that LastPass cannot provide your password if you lose it.
The developers work on the development system, which has only the resources needed to write and debug code. No user data will be on the development system. Developers test their code on the dev server to confirm that it will run properly with the rest of the application. When the code has passed all tests on the dev server, it's moved to a staging server for more robust testing. The staging server also has no user data, but it does have data that's designed to look like user data. After testing on the staging server, the code is either moved to the production server or, if flaws were identified, the developers receive feedback and continue working on the development server.
So simply being able to see the source code doesn't introduce any vulnerabilities. Even if an intruder managed to modify the source code, the changes should be spotted while still on the development server or during testing on the staging server.
LastPass says there is no evidence that the incident involved any access to customer data or encrypted password vaults and that all products and services are operating normally. LastPass also set up a blog post dedicated to providing more information on the incident.
Windows 10 and Windows 11 computers have programs that came with the computer or can be downloaded from the Microsoft Store, but where are these applications installed? You won't find them in the Program Files directory or the Program Files (x86) directory. Where are they?
App files are in a hidden directory called "WindowsApps". All Windows apps that you install or that came with the factory version of Windows 10 or 11 are there. Maybe you'd like to see what's there.
CAUTION: Look, but don't touch. Microsoft protects this directory for a good reason. What I describe here is safe, but don't add, modify, or remove files in the WindowsApps directory.
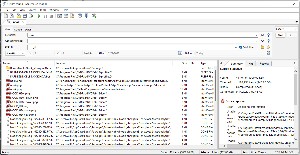 I have the Barnes and Noble Nook reader app. If I try to find it using Agent Ransack, I'll see a list of data files and log files in the AppData folder and elsewhere, but not the application files that I know are in the WindowsApps directory.
I have the Barnes and Noble Nook reader app. If I try to find it using Agent Ransack, I'll see a list of data files and log files in the AppData folder and elsewhere, but not the application files that I know are in the WindowsApps directory.
Searching for how to open WindowsApps will lead to many convoluted descriptions. TechRepublic explains that you can use the Shell command to open the WindowsApps directory, but then has to explain how to use the Shell. There are lots of good reasons to use the Shell, but this seems like it might not be one.
GeekFlare omits discussing the use of Shell to open WindowsApps, but it offers three other options:
Why all the complex options? If you want to see WindowsApps, all you need to know is that it's located inside the Windows directory.
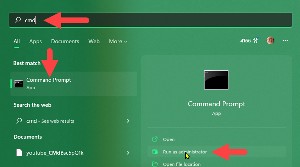 Step One: Open CMD as an administrator.
Step One: Open CMD as an administrator. Step Two: Type cd "C:\Program Files\WindowsApps".
Step Two: Type cd "C:\Program Files\WindowsApps".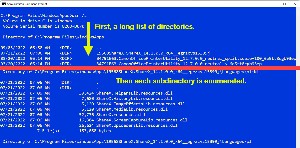
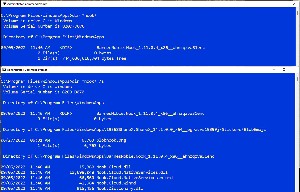 To see a list of directories and subdirectories, type dir /s (left) or to see all of the files associated with the Nook Reader, type dir *nook* /s.
To see a list of directories and subdirectories, type dir /s (left) or to see all of the files associated with the Nook Reader, type dir *nook* /s.
 Admittedly, if you want a view that's easier to read, you'll need one of the more involved processes and TechRepublic's process is the best option for just viewing which applications are there, but that's all you can do. Clicking the icon for the Nook Reader will start the app. Right-clicking allows me to pin or unpin the app on Start Menu or the Task Bar or to create a shortcut. That's all.
Admittedly, if you want a view that's easier to read, you'll need one of the more involved processes and TechRepublic's process is the best option for just viewing which applications are there, but that's all you can do. Clicking the icon for the Nook Reader will start the app. Right-clicking allows me to pin or unpin the app on Start Menu or the Task Bar or to create a shortcut. That's all.
Because it's important not to meddle with files in the WindowsApps directory, nothing more complicated is needed.