Listen to the Podcast
16 September 2022 - Podcast #810 - (22:44)
It's Like NPR on the Web
If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.

If you find the information TechByter Worldwide provides useful or interesting, please consider a contribution.
Smart phones are popular because they're really tiny computers that fit in a pocket, browse the web, send instant messages and email, take photos, and occasionally are used to make phone calls. Because they do so much, a hacked or stolen smart phone is more than just a gigantic inconvenience. Protections may eliminate the problem and preparations can help recover if something bad does happen.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
 Losing a phone is easy because these devices are small. They're also attractive to thieves.
Losing a phone is easy because these devices are small. They're also attractive to thieves.
Start with protections such as using facial recognition, a fingerprint scanner, a long security code, or a pattern. Ignore 4-digit PINs because they offer little protection. Using a fingerprint or facial recognition means you won't need to enter the long security code frequently. In some cases, you may be able to pair a phone with a smart watch so that it stays unlocked for some period as long as the devices are close to each other.
The phone should automatically lock and, although this slows access to the phone, it's a lot better than having a thief gain access to all of your data.
If the smart phone offers a "find" feature, be sure to enable it. On most Android phones, go to Settings > Security and make sure that Find My Device is enabled. Some Android devices call this feature "Find My Mobile" and place it elsewhere on the menu. For IPhone users. go to Settings > Your name and enable Find My IPhone. You can share your location with friends and family, see your device's location even when it's offline, and send the phone's location to Apple when the battery is critically low.
Make sure that automatic backups are enabled. This is useful when you acquire a new phone and makes the transition easier even if the phone is never lost or stolen.
Many experts recommend not storing passwords and other sensitive information on the phone and that's good advice in general. However, the alternatives are just as bad. Nobody can remember hundreds of passwords and carrying them in a notebook is even worse. Instead, install a password manager such as LastPass or 1Password that offer a version for your smart phone. Password managers require a master password and that password should definitely not be stored anywhere on the phone.
 One common way that scammers gain access to the information on phones is by using social engineering to convince users to install malicious apps. This is more of a problem for Android users, but IPhone users aren't exempt. Download apps only from the app store, and be careful even then. Some bad apps have been known to get through. If you absolutely trust a vendor, downloading an app without going to the store is acceptable, but be careful. Also, examine what permissions apps want. Many request far more privileges than they require.
One common way that scammers gain access to the information on phones is by using social engineering to convince users to install malicious apps. This is more of a problem for Android users, but IPhone users aren't exempt. Download apps only from the app store, and be careful even then. Some bad apps have been known to get through. If you absolutely trust a vendor, downloading an app without going to the store is acceptable, but be careful. Also, examine what permissions apps want. Many request far more privileges than they require.
And while we're on the subject of apps, it's important to keep them up to date because many of the updates address security issues. Keeping both the phone's operating system and the apps up to date improves security. Examine the apps you have installed occasionally, too, and delete ones that you don't use.
Android phone users can program a message on the lock screen. Mine asks that the phone be returned to me and lists my wife's phone number. This is a good safeguard if the phone is lost and then found by an honest person, but not of much use otherwise. If your phone doesn't have this option, consider taping a small note to the back of the device.
Any app that allows for two-factor authentication should have that feature enabled. This is another choice that slows access to your data, but it's immensely more secure using SMS messages and authenticators such as those from Google and Authy. Adding that second security key will stop most scammers in their tracks.
Unless you're using your smart phone at home with a Wi-Fi connection to your own router, enable a virtual private network (VPN). Google provides an automatic VPN for its Google Fi phones. If your phone or your service provider doesn't include a VPN add one and enable it whenever you're away from your own Wi-Fi connection.
 Some unique numbers are associated with your smart phone. These numbers can be used to identify your phone if it's stolen, so write down the IMEI (International Mobile Equipment Identity) number or MEID (Mobile Equipment Identifier) number. These numbers are part of the phone itself, unlike information stored on the phone's removable SIM card. If you have the phone's IMEI or MEID, it can be added to a list of lost and stolen phones, which at least makes it difficult to sell or activate on another network. You should be able to display this information by opening the phone app and dialing *#06# to display several important numbers.
Some unique numbers are associated with your smart phone. These numbers can be used to identify your phone if it's stolen, so write down the IMEI (International Mobile Equipment Identity) number or MEID (Mobile Equipment Identifier) number. These numbers are part of the phone itself, unlike information stored on the phone's removable SIM card. If you have the phone's IMEI or MEID, it can be added to a list of lost and stolen phones, which at least makes it difficult to sell or activate on another network. You should be able to display this information by opening the phone app and dialing *#06# to display several important numbers.
To prepare for the worst, learn how to wipe all of the data on your phone remotely. The process varies by phone and by service provider. If the phone is missing and you're reasonably certain that it has been stolen, see if the Find My Phone feature can tell you where it is or have someone call it. If the phone has just been misplaced, that might resolve the issue instantly. If not, immediately wipe the phone's data. (You do have a backup, right?)
 Then file a report with police, the phone service provider, and your insurance company. It would be a good idea to contact your bank to have accounts frozen if the phone contained financial information.
Then file a report with police, the phone service provider, and your insurance company. It would be a good idea to contact your bank to have accounts frozen if the phone contained financial information.
Even if you have a password manager that has its own strong password that isn't stored on the phone, it's a good ideal to change all sensitive account passwords immediately. That includes email accounts, banking and financial institutions, and stores.
If you're lucky and you're able to recover the phone, perform a factory reset and reload everything from backup. This is an important precaution because you don't know what someone has done with the phone while it was out of your possession.
With luck, you'll never need to perform any of recovery tasks, but it's good to know what they are just in case because there's somebody out there who would really like to have your smart phone.
We can't eliminate mistakes and stupidity, but we can ensure that some stupid events can be recovered from. What we need is something that will save our data when undo doesn't work or isn't available.
There's no undo if some small group of humans starts a worldwide nuclear war. That would be Game Over. Likewise, if we fail to account for climate change, it won't be the end of the planet but it will be the end of homo sapiens and many other life forms. The planet got along quite well without us and can do so again. So those aren't the kinds of things to consider in this context.
Instead, think about the Oh-No Second. Tom Scott, a British technology writer with a YouTube channel may not have coined the term "ohnosecond", but he used in in a video he made a couple of years ago. "The ohnosecond," he says, "is the second after you make a terrible mistake — the second you realize what you just did."
I've experienced some ohnoseconds. Two memorable ones occurred in the early 1990s and in May of 2000.
I was in the process of replacing the data drive in my computer in the 1990s. In those days, disks had to be initialized and then formatted before they could be used. The computer had two disk drives, so I connected the third one and started the low-level format process on the new drive. That was fine, except that I wasn't running a low-level format on the new drive; I was running it on the boot drive.
Despite canceling the process within approximately 1.5 ohnoseconds, the boot drive was no longer usable. Fortunately, I had a backup and fixing the problem, while annoying, was at least possible.
The event in May of 2000 involved the "I Love You" virus that infected over 10 million computers on a single day and at least 50 million were eventually compromised. Mine was one of them. In fact, it was the office computer. I opened the attachment in a message that appeared to be from a co-worker. The attachment masqueraded as a harmless text file, but was in fact a Visual Basic script that started sending copies of itself to everyone in the company. Fortunately, I recognized what was happening, instantly yanked the network cable, and notified the chief security officer. The malware got no further than my computer, but it started overwriting program files and image files with copies of the virus.
Despite quick action, the damage had been done even though it was limited to a single computer. After removing the virus from my computer, I had to get the damaged files back. Once again, backup saved the day. Files on my computer had been backed up to corporate servers, so all I had to do was restore them.
Backup saved the day in both of those cases, but it was a different story for Tom Scott who describes the event in his 11-minute YouTube video called "The Worst Typo I Ever Made." He committed the typo around 2005 when he wasn't yet 20 years old. What's remarkable is that he's willing to share the experience because it's clearly an embarrassing incident.
But he tells the story well, even that part that didn't work out so well. What really went wrong was that a simple change didn't do what it was supposed to do because of a single typo. He was working on a live copy of the database. He hadn't issued the command using a technique that would allow him to roll back the changes. And there was no backup.
You probably see the common thread in my two events and in his: Backup.
Spare eleven and a half minutes to watch this video. Pay particular attention to the comments around the nine-and-half minute mark.
The Word "Excel" conjures "spreadsheet" or "analysis" or "math" for most people. Perhaps "calculations" or "budgets" or "accounting". All of those are valid, but Excel has some powerful text capabilities, too.
Maybe you use Excel to track names and addresses for holiday cards. Then you can use it with Outlook or another email application to send holiday emails, or with Word's mail-merge function to create mailing labels and maybe even personalized holiday letters.
Click any small image for a full-size view. To dismiss the larger image, press ESC or tap outside the image.
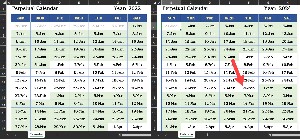 Excel can be used to create a useful perpetual calendar. Fill in the year and Excel will create the dates. This is based on work by Leila Gharani, a Microsoft MVP who knows a lot about a wide range of topics. She lives in Austria and has a master's degree in economics; I recommend her YouTube channel. I checked the function of the calendar and noted that it correctly shows that 2024 is a leap year.
Excel can be used to create a useful perpetual calendar. Fill in the year and Excel will create the dates. This is based on work by Leila Gharani, a Microsoft MVP who knows a lot about a wide range of topics. She lives in Austria and has a master's degree in economics; I recommend her YouTube channel. I checked the function of the calendar and noted that it correctly shows that 2024 is a leap year.
You can download the Perpetual Calendar Excel file from the TechByter website. The sheet is protected so that only the year may be changed, but it is not locked with a password so anyone can change it.
This is the primary formula that occupies the first Sunday cell of the calendar and replicates itself automatically to 53 lines. It uses the DATE function and the WEEKDAY function to determine the appropriate date for each cell.
=SEQUENCE(53,7,DATE(H1,1,1)-WEEKDAY(DATE(H1,1,1))+1,1)
Conditional formatting is applied to display the date in light gray when the date value is not in the current year, which is in cell H1. If this condition is met, the second conditional rule is ignored.
=$H$1<>YEAR(B4)
The second conditional formatting rule applies a light green shade to the dates in each month when the MOD condition is satisfied.
=MOD(MONTH(B4),2)
The explanation of how to create this calendar is on YouTube.
But Excel has had powerful text functions for a long time and Microsoft's developers have been creating new functions and processes that help users deal with text in the application. It really is a versatile application to use in preparing data for use in other applications, and the data need not be numeric.
The current version of Excel has more than three dozen text functions. Four of those functions were added in the 2013 version, one in the 2016 version, and six in the Microsoft 365 version of Excel.
Don't mistake Excel for InDesign, Word, or even a basic text editor. Although people have used Excel to create text documents, this is more of a misuse than a use — comparable to using a pair of pliers as a hammer because you don't have a hammer. Or using a subcompact car to move your belongings across town instead of renting a truck. Using the right tool for each job is wise, but within the context of normal spreadsheet operations, it's not uncommon to encounter the need to manipulate letters and words in addition to numbers.
In addition to the nearly 40 functions that are designed explicitly for manipulating letters and words, Excel has functions such as XLOOKUP and Text-to-Columns that can be used with numeric or text values. Text-to-Columns has been around for a long time and it's a lifesaver when you have data that includes multiple bits in a single field. Let's say you've received a text file or an Excel file that contains a people's first and last names in a single column. If you need to be able to use the first name and last name independently, Text-to-Columns is the perfect way to split the information in the name column into columns for the first name and the last name.
Some of the new features in the Microsoft 365 version make the process even better. TEXTSPLIT breaks the text in a column into multiple columns based on delimiters. This function can split text into multiple columns or multiple rows. TEXTSPLIT can deal with one of the most common problems faced by the Text-to-Columns function. Not every name in a name field will have just a first name and a last name and a well-written TEXTSPLIT function can deal with the presence of middle names or initials and name suffixes.
To see a list of Excel's explicit text functions see Microsoft's Excel support website.
Excel has included data validation functions for quite a while now with Auto Lists, but the Microsoft 365 version adds more flexible validation functions. Auto Lists allowed users to create dropdowns that included all valid entries. Users could list the 50 state abbreviations as valid entries. You'll find quickly that you need to add the District of Columbia, Puerto Rico, and our other imperialistic possessions. That's not too bad because the full list is less than 100, but what if you need to give users the option to choose from thousands of possible model numbers? A combo box form control responds when users start typing. Excel will display a list that matches what the user has typed.
So Microsoft has added AutoComplete to dropdown lists for Microsoft 365 versions of Excel. Create a dropdown list the way you usually would with the Data Validation feature. When the user starts typing, a match will be automatically entered. If multiple possibilities exist, the user can select one and press Enter.
I said that Microsoft 365 users have half a dozen new text features. On the day I wrote this, these were still in the beta version of Excel. It's likely that they will be included in the general release, but there are no guarantees. Here's a list.
These are in addition to the existing text functions such as:
In total, Excel has around 500 functions, including those for compatibility, cube operations, database manipulation, date and time functions, engineering operations, financial calculations, logical functions, lookup and reference actions, math and trigonometry functions, statistical calculations, and web functions.
There are many online tutorials for Excel and Spreadsheeto even lists the 30 functions every Excel user needs to know. If you use Excel, but haven't explored more than the basic few functions, learning more about them is almost sure to make your life easier.